Before addressing the matter proposed in our headline let’s put a few disclaimers out there for the sake of legality: Almost everywhere around the world the act of having access to the personal computer of a third party without their approbation is considered a felony and a prosecutable act by law enforcement agencies. However, doing so with legal permission is one of the many protocols used by many computer system companies to provide customer support. If you feel the need to learn about the legal aspects regarding the use of RAT systems, it would be better if you consult a lawyer or do some research online on your country.
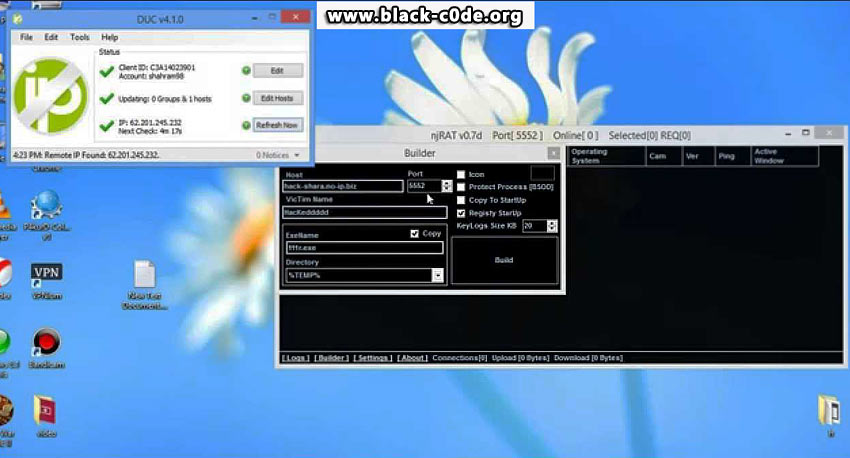
With that little tidbit out of the way not we can go over the subject. RAT is an abbreviation for “Remote Administration Tool.” It is also known by another name that it doesn’t sound pretty at all: Remote Access Trojan. The original purpose of such software is completely white-hat, made to remotely control your own or company’s computer servers from another physical location. However black-hat hackers noticed an opportunity in this operation and started using it for their malicious campaigns, with using all such similar apps which exist nowadays.
While the various RAT software variations, made with different programming languages have been (more…)
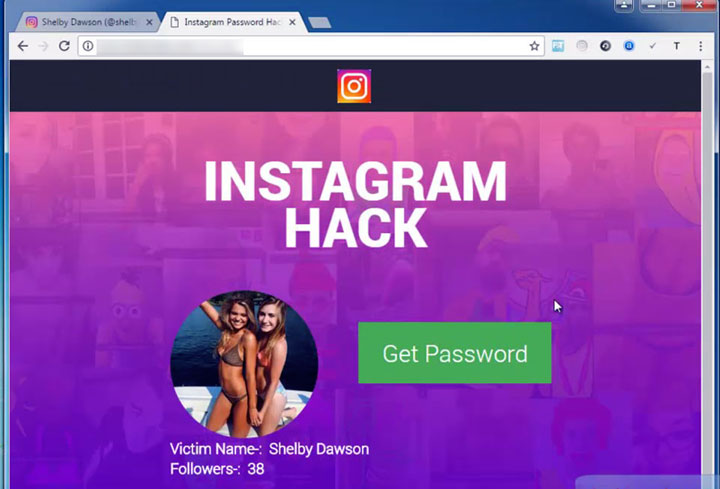



 In this post I’m going to do an in-depth analysis about the email hacking software “
In this post I’m going to do an in-depth analysis about the email hacking software “